Protective DNS, (aka PDNS or Secure DNS) will be the best performing and highest ROI security control you implement this decade. But before investing in a solution, gain an understanding of what PDNS is, its capabilities, critical considerations, and how to best implement it for both security and privacy.
Protective DNS (PDNS) is easily deployed, proactive, and protective of everything that connects to the Internet by nature - few security products can make those claims. Thanks to new guidance out from NSA and CISA, there’s a lot of buzz and vendor noise about PDNS right now, and to help you make sense of it we’ve cut through the fluff with key takeaways and vendor selection criteria from the NSA and CISA on implementing PDNS.
PDNS is in ThreatSTOP's DNA. We've been a DNS Security provider for over a decade, and the Domain Name System itself was invented by our Chief Scientist, Dr. Paul Mockapetris. ThreatSTOP's technology enables organizations to turn their existing DNS into Protective DNS by adding a simple and affordable cloud service - no new hardware, no big network changes, no touching every endpoint. Other PDNS providers can't do that, certainly not affordably and at scale.
Since we launched DNS Defense, the market has been flooded with companies asking for your DNS traffic in order to “protect” it, or trying to sell you expensive appliances to do it. But effective PDNS doesn’t require any of that. You'll always be safer, more in control, and save money designating and managing your own DNS. It’s easy, and costs are minimal.
What is PDNS?
The term PDNS came to prominence in January of 2021 after the NSA (National Security Agency) and CISA (Cybersecurity and Infrastructure Security Agency) published a guide to Protective DNS Services. This followed NSA guidance from earlier that month recommending organizations use only enterprise-designated DNS resolvers, and avoid 3rd party resolution, encrypted or not. These statements, and the guidance, make a clear endorsement of two DNS security must-do's:
- Controlling your own designated DNS resolvers
- Making your DNS protective by not resolving potentially harmful DNS requests
PDNS Vendors
There are perhaps over 100 DNS security vendors today, but the NSA-CISA guidance covers only 8 commercial providers that already sell PDNS to the Government. Should you consider these 8 providers? Yes, of course - and others too. As a vendor of PDNS, we find the list of capabilities in the guidance (and in the figure below) to be incomplete, missing important considerations such as:
- Privacy
- False positive rates
- Reporting
- Custom lists
as well as a slew of other critical capabilities. But to be clear, ThreatSTOP’s DNS Defense and MyDNS products easily meet and exceed the requirements listed in the NSA-CISA guidance. Take a look:
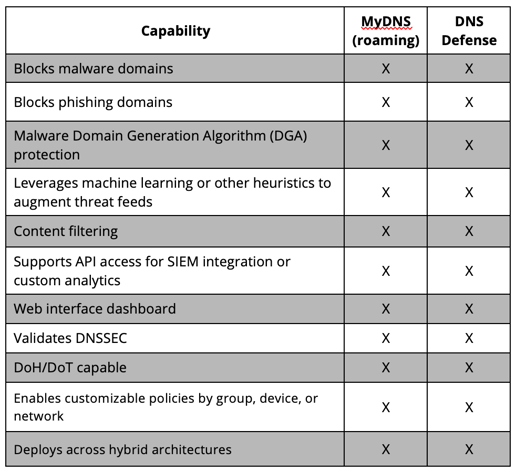
Beyond the capabilities listed by NSA-CISA, organizations should also consider the following when selecting a PDNS solution:
- Privacy. What can be construed from the DNS requests made by users and devices in your network? Forwarding DNS to a 3rd party might be considered an operational security breach by some.
- Threat Intelligence Coverage and Quality. PDNS’s ability to identify and prevent threats relates directly to the quality and coverage of threat intelligence. We aggregate over 900 TI feeds.
- Required Hardware and Software. ThreatSTOP has a different approach to PDNS: We’re a cloud service that integrates with any DNS platform you have today, or tomorrow. If you don’t have one, we will help you set up a free one on-prem or in the cloud.
- Effort and Ease-of-Use. Does your PDNS solution reduce the load for your stretched security team? Or does it add more data and work to the growing pile? How much time will be required to manage it?
- Reporting and Remediation. A PDNS solution isn’t complete unless it can pinpoint the host machine that made a harmful DNS request, so the machine can be quarantined, analyzed, or remediated.
Why PDNS?
The DNS is not inherently secure, it is frequently abused, and DNS is a vector used in many attack types ranging from Denial of Service (DDoS) to data theft via DNS Tunneling. DNS-related attacks are growing quickly, and PDNS is being promoted as a pragmatic solution.
PDNS is not a security-related change to the DNS protocol; it’s a security service that augments how DNS works, enabling it to be a security control that identifies and prevents DNS resolution of malicious domains, or when other elements are known to be bad such as the IP address resolved to, the authoritative nameserver name or IP address.
PDNS and the CMMC
It’s not just the NSA and CISA pushing DNS security to the forefront. Due to the criticality of securing DNS, the Department of Defense (DoD) included DNS filtering as a requirement in its new Cybersecurity Maturity Model Certification (CMMC) standard (SC.3.192). The DoD has added new language around DNS filtering to its security standards, making PDNS a prerequisite for Maturity Level 3.
DNS Privacy
Privacy considerations should be at the foremost when considering PDNS providers. If the guidance and requirements from the NSA-CISA and DoD are taken seriously, as they should be, having any DNS servers performing resolution other than your own designated DNS servers introduces risk and runs counter to the guidance provided. For some, 3rd party visibility to your DNS traffic has serious implications (e.g. HIPAA and Financial PII).
Security Reporting
Blocking a DNS request nets immediate security value, but you may find that malicious DNS queries can be a symptom of an infection. Granular reporting that indicates the querying host, the DNS request, date and time, and why the DNS request was prevented are all critical to performing security-enhancing actions after the initial block.
DNS Policies
No two organizations are the same, including what they classify as malicious or unwanted. Do you allow Facebook on work machines? Shopping on Etsy? Can employees use a proxy? For some these may be security concerns. ThreatSTOP customers build custom policies. You should consider how well pre-built policies would work for you if you choose to go that route.
Final Considerations
Using a PDNS provider as part of your overall security strategy is likely to become the standard for enterprise organizations, government agencies, educational institutions, and other businesses that are at a high risk for network security attacks.
Ease of deployment is crucial. Your organization may need to roll out a solution swiftly, and will want PDNS that can be implemented within your timeframe and budget constraints.
Roaming Clients are essential, especially in a work-from-home environment where users are no longer protected by the company network. These users might be working on personal devices that have no security software installed - increasing your company’s security risk. ThreatSTOP's MyDNS offers protection for Windows and MacOS by providing a critical first layer of protection no matter where your employees are working from.
Content filtering capabilities are an added benefit of a PDNS service. They allow your organization to block inappropriate content such as pornography, social media, gambling sites, etc. And you can implement this content filtering through custom policies to give you control over who sees what content based on role, department, or group.
Like to read more? We've published a full PDNS Solution Guide on securing DNS here.
What about an expert-led demo to see how it works? Ready to start a PDNS trial today?
