Connect with Customers.
Disconnect from Risks.
Microsoft Azure

Protecting Azure is easy and affordable. ThreatSTOP blocks malicious and unwanted traffic from breaching your virtual network, and prevents communication with attacker infrastructure to keep cloud workloads clean.
ThreatSTOP's Platform delivers customizable security policies to virtual enforcement devices. These enforcement devices block inbound and outbound threats over TCP/IP and DNS using continuous threat intelligence updates.
ThreatSTOP helps you secure your Azure network with advanced, threat-intelligence powered solutions used to secure physical networks all over the world. Cloud native, deploys in minutes, and fully automated. We've simplified security for Azure:
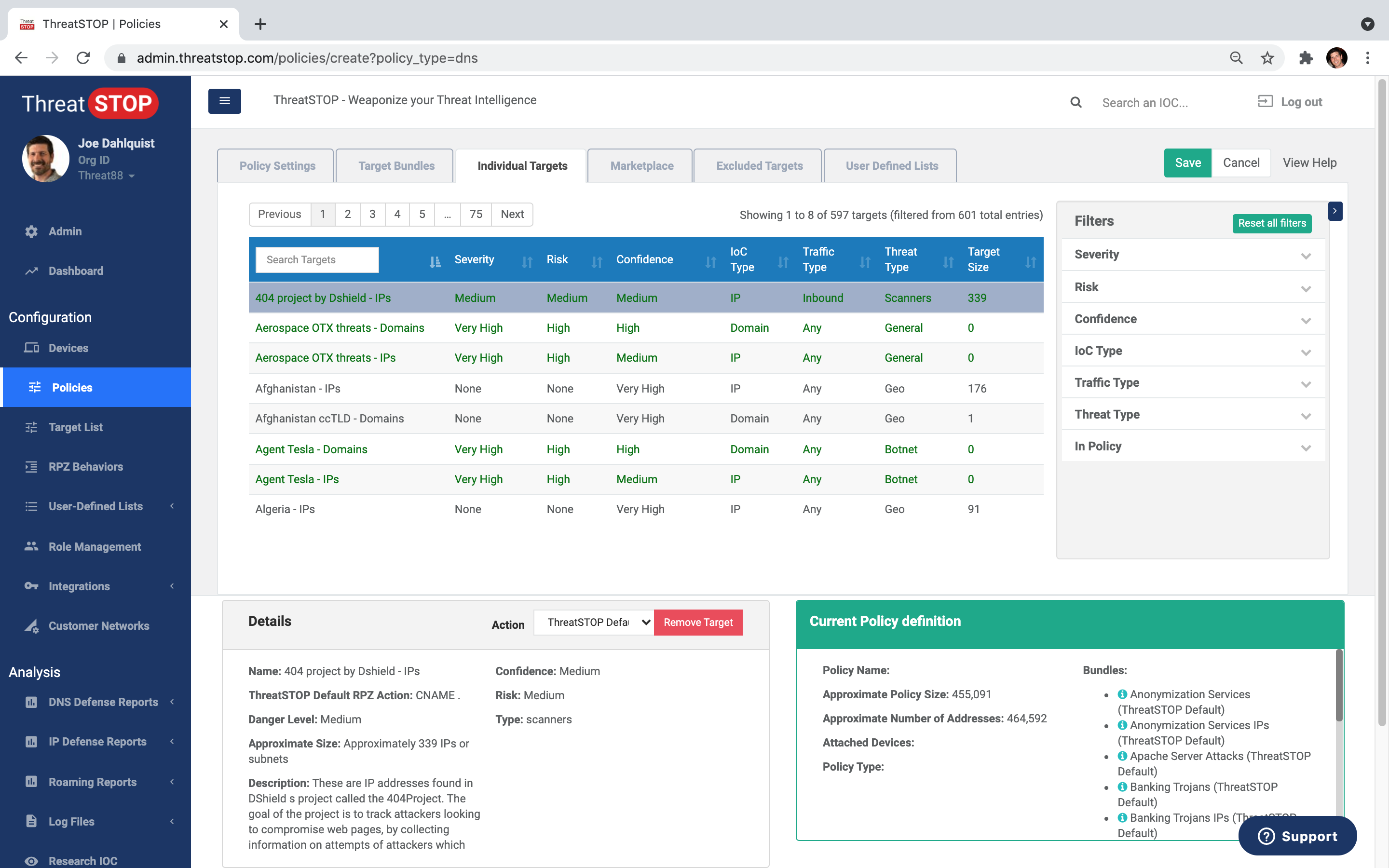
- Create security policies in the ThreatSTOP portal to protect against threat types, geographic locations, and specific IPs and domains
- Configure VMs in your Azure network to receive automated policy updates from ThreatSTOP
- Real-time attacks are blocked and reported, while safe inbound and outbound traffic is allowed to pass
- View detailed information about the threats blocked to make investigation and remediation fast and effective
See How We Do It
Intelligence collection
We incorporate hundreds of threat intelligence feeds that are human & machine curated, delivering the broadest coverage in the industry of IP addresses and domains.
Policy customization
Get 600+ fully customizable policies in selectable categories. Tailor your own custom block & allowlists.
Device integration
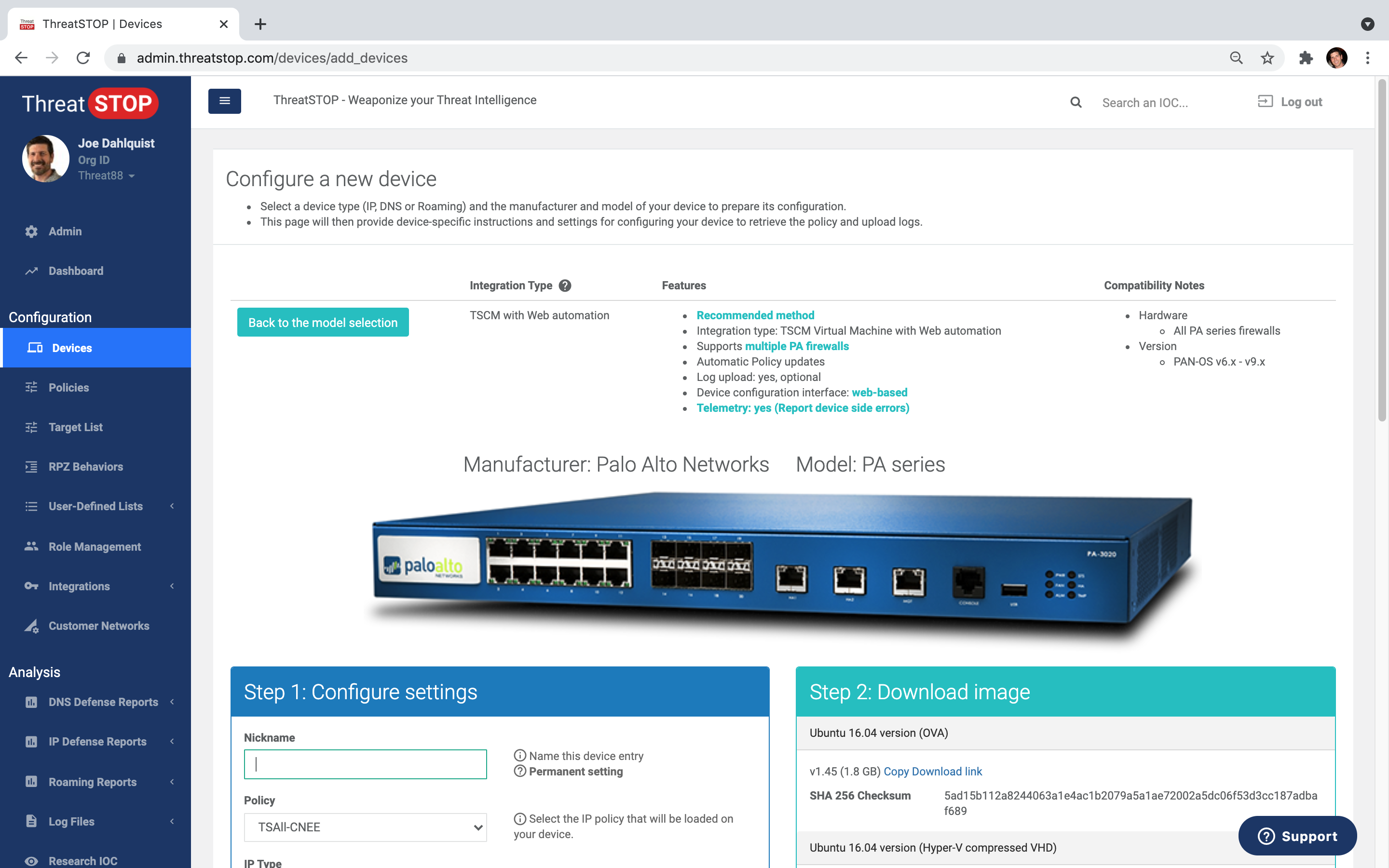
Automated policy updates NGFW, DNS, Router, Switch, IDP, WAF, SIEM and more.
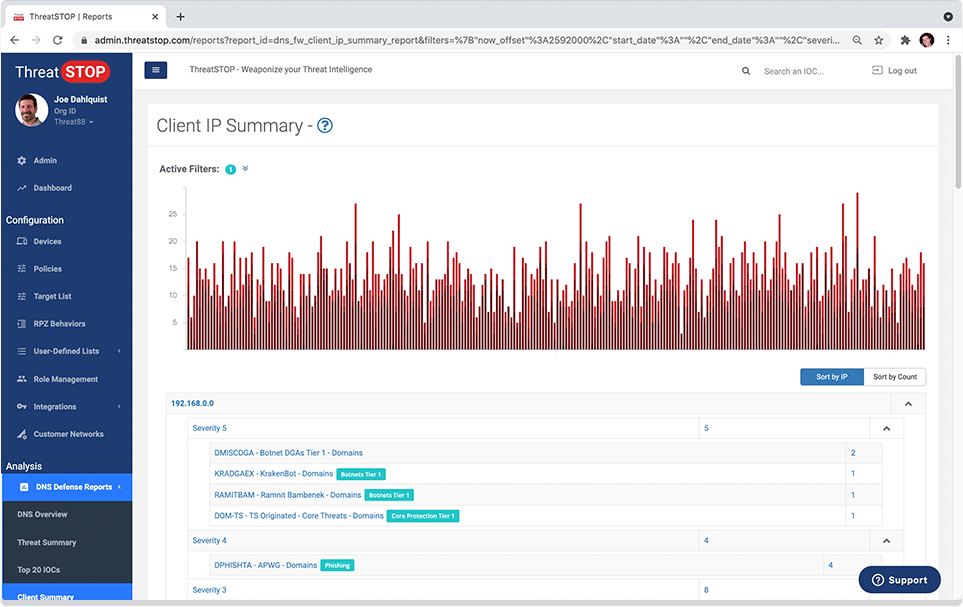
Advanced reporting
View & analyze blocked threats. Identify affected client devices. Custom email reports & alerts.

Save Time
- Automate and outsource essential 24/7 security policy updates.
- Rich reports in our portal or your SIEM.
- Rapidly identify infected hosts.
- Research tools, like Check IOC, included.
- Customize and schedule email reports and alerts.
Save Money
- Add powerful security to existing devices.
- Reduce endpoint infections and stop breaches.
- Reduce load on existing security layers.
- Eliminate unwanted bandwidth usage.
- Increase security and network efficiency.
Be More Secure
- Block connection attempts to criminal infrastructure on all ports and protocols.
- Continuous, automatic policy updates.
- Unique and valuable telemetry for SOC's and MSP's.
- Customize policies to match security postures.
- Multivendor security is always a feature, not a bug
Start a 30-day trial
Try ThreatSTOP in your Azure environment. No strings, no bull$#%, and it takes just minutes to setup. Let's secure that cloud.
How to deploy
Getting started is as simple as 5 easy steps.
Sign up for the service
Pick a security policy to use
Integrate ThreatSTOP with Azure
Start automatically blocking threats
See reports detailing the protection
ThreatSTOP Platform
The ThreatSTOP platform is a SaaS security platform with modular product offerings for Protective DNS (PDNS), firewall automation, and other Threat Intel use cases. It integrates with physical, virtual, and hosted security stack components including firewalls, DNS servers, IDPS, SIEM and more. The platform automates threat intelligence acquisition, curation, and timely application for threat mitigation and visibility. Modules include:
DNS Defense
Using continuous updates from hundreds of Threat Intelligence sources, DNS Defense stops dangerous and unwanted DNS traffic before damage is done.
IP Defense
IP Defense sends automated policy updates to existing firewalls, routers and switches, and stops inbound attacks at network edges, before damage is done.
MyDNS
This takes the network DNS Defense Service and delivers it to individual endpoints, providing the same security even when these endpoints are outside the corporate network.
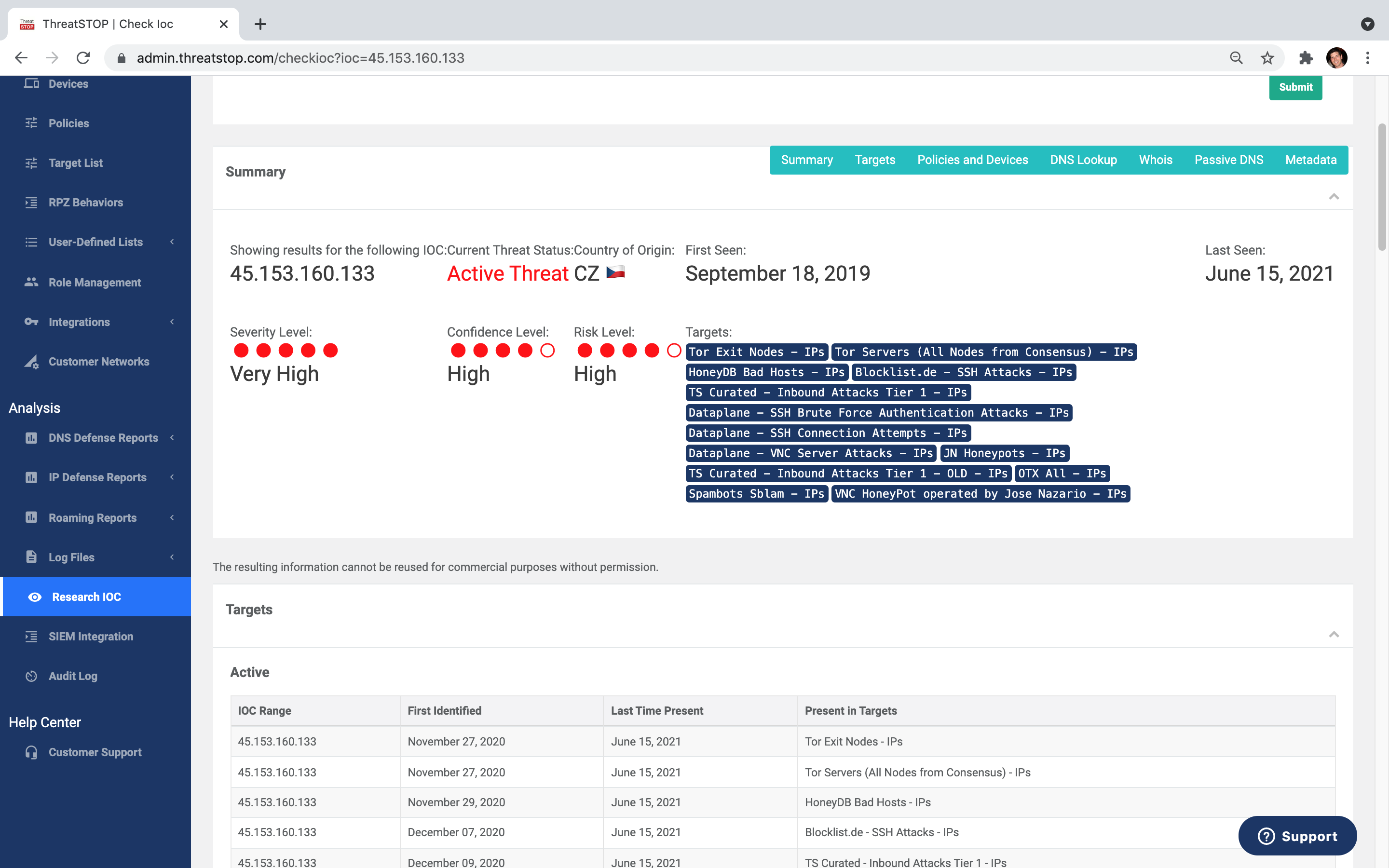
Check IoC Subscription
Check IOC is now available as a standalone subscription. We've made it easy to get your hands on tools that give you invaluable data, backed by one of the largest databases that we've been building for over a decade.
ThreatSTOP CE
The ThreatSTOP Community Account is our way of saying thank you to the security community for everything they do. A Community Account entitles you to run ThreatSTOP on one IP device (firewall, router, etc.) and one DNS device. Community accounts are limited to pre-built policies that include core protections such as the DShield Blocklist and Emergency Handler Blocks.
- DNS Defense CE
- IP Defense CE
- MyDNS CE
- Check IoC Tool
Threats blocked today
Updated every 15 minutes
Free Trial
See what your other security products have been missing. Start Stopping Threats today at the DNS layer. Quick, easy setup.
