Connect with Customers.
Disconnect from Risks.
IP Defense
IP Defense is a Cloud-native service that works with popular TCP/IP-based devices like firewalls, routers and switches, load balancers, and IDPS. ThreatSTOP’s service enables these devices to identify and stop threats early, before they cause damage. Powered by continuous updates from hundreds of Threat Intelligence sources, the platform knows and tracks the infrastructure used by cyber criminals to conduct attacks, and keeps your network devices updated to block those malicious IP sources and destinations.
Add in predictive feedback loops and customer-specific block and allow lists, and you have ThreatSTOP's highly adaptive firewall protection. There is no new equipment to buy, or threat intelligence sources to tap into - ThreatSTOP provides the data, the integrations, and the automation to keep your perimeter tuned for the newest threats.
- Turns NGFW, Routers & Switches into automated security gateways
- Drops or redirects IP/CIDR threats before damage is done
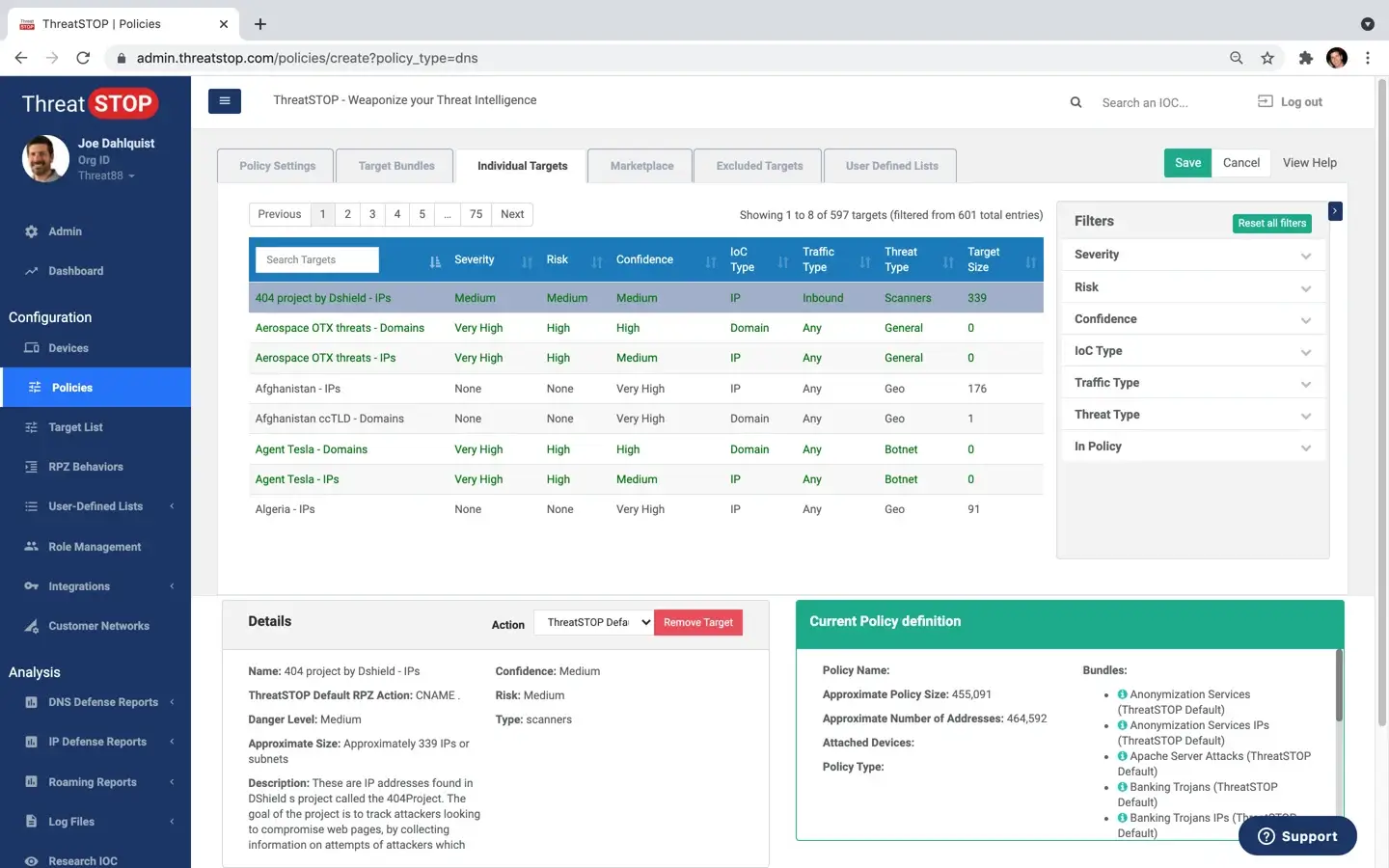
- Has highly customizable policies that natively integrate with your devices
- Supports your custom, in-house, or 3rd-party threat intelligence feeds
- Includes powerful reporting and security research tools

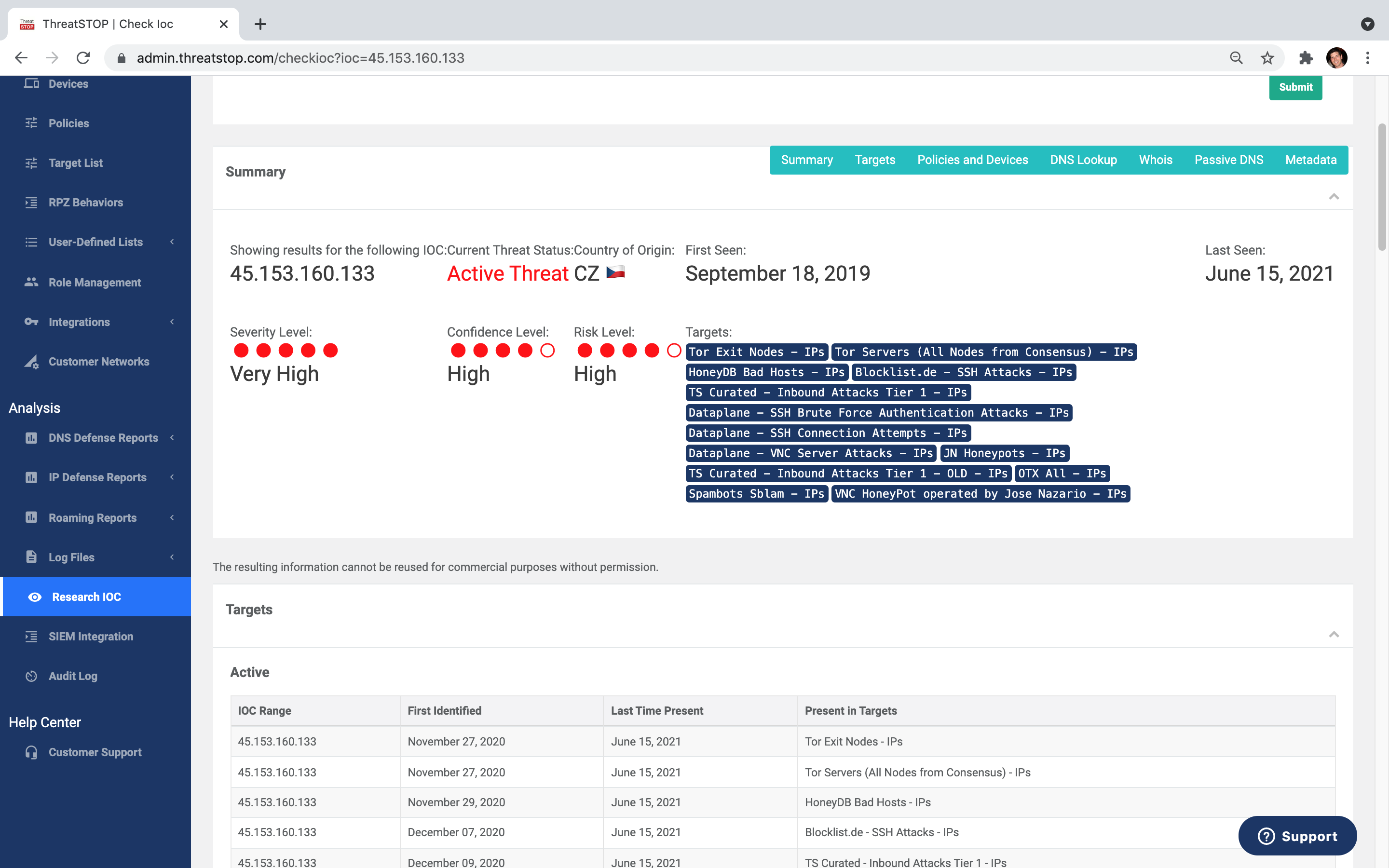
Get 600+ fully customizable policies in selectable categories. Tailor your own custom block & allowlists.
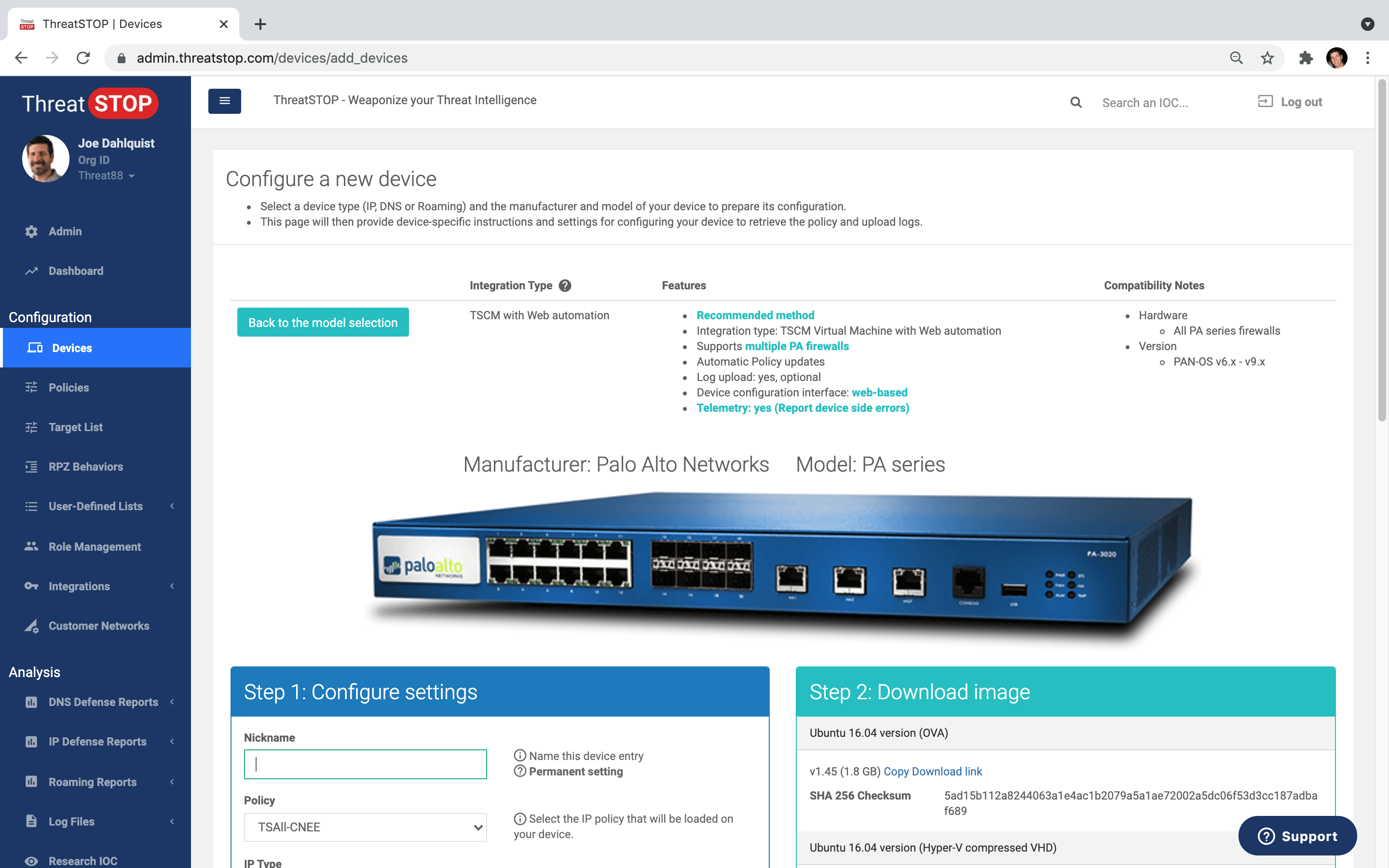
Automated policy updates NGFW, DNS, Router, Switch, IDP, WAF, SIEM and more.
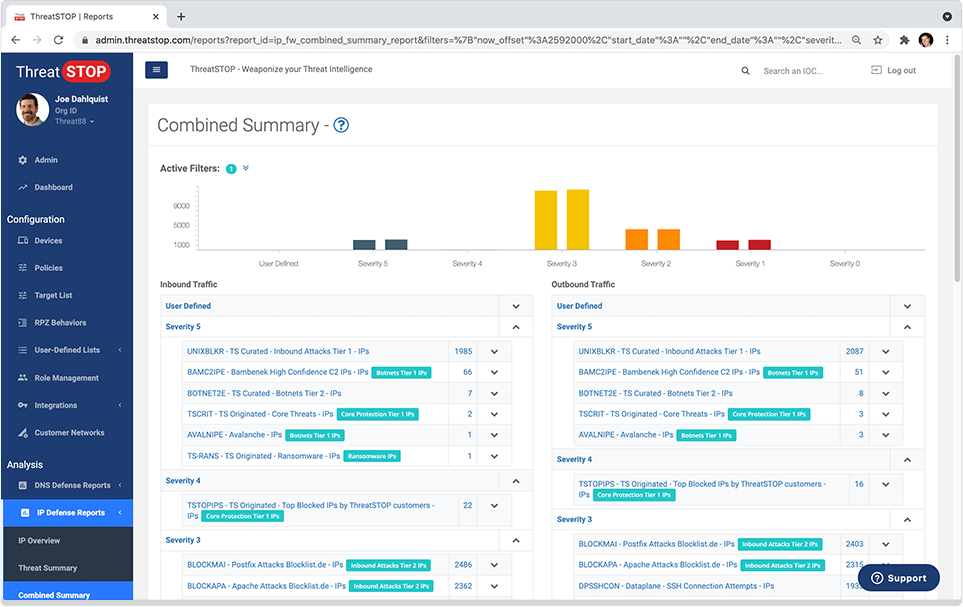
View & analyze blocked threats. Identify affected client devices. Custom email reports & alerts.
Save Time
- Automate and outsource essential 24/7 security policy updates.
- Rich reports in our portal or your SIEM.
- Rapidly identify infected hosts.
- Research tools, like Check IOC, included.
- Customize and schedule email reports and alerts.
Save Money
- Add powerful security to existing devices.
- Reduce endpoint infections and stop breaches.
- Reduce load on existing security layers.
- Eliminate unwanted bandwidth usage.
- Increase security and network efficiency.
Be More Secure
- Block connection attempts to criminal infrastructure on all ports and protocols.
- Continuous, automatic policy updates.
- Unique and valuable telemetry for SOC's and MSP's.
- Customize policies to match security postures.
- Multivendor security is always a feature, not a bug

