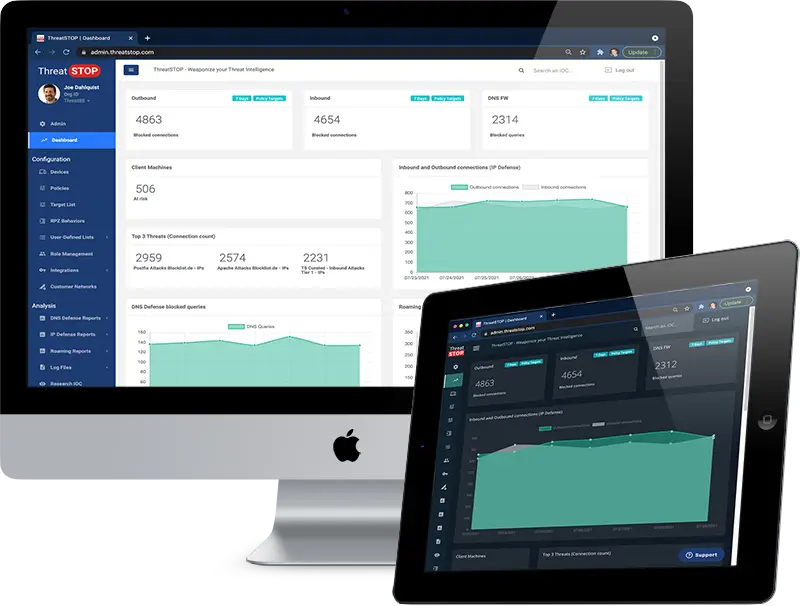
How Protective DNS Works
Proactively stop threats, at the DNS layer, before the malicious content gets into your network. ThreatSTOP is the most comprehensive, advanced and up-to-date real-time DNS Filter available. Blocks malicious DNS resolution requests and IP connection attempts across 600+ categories from billions of data points. Easily integrates with DNS, DDI, Firewalls, Routers and Cloud Native infrastructure.
Protective DNS Security
Protect clients, remote users and servers from phishing, ransomware, malware and more.
Protect Web and Server Infrastructure
Cut credit card fraud by 50%, stop bots and unwanted traffic from impacting operations.
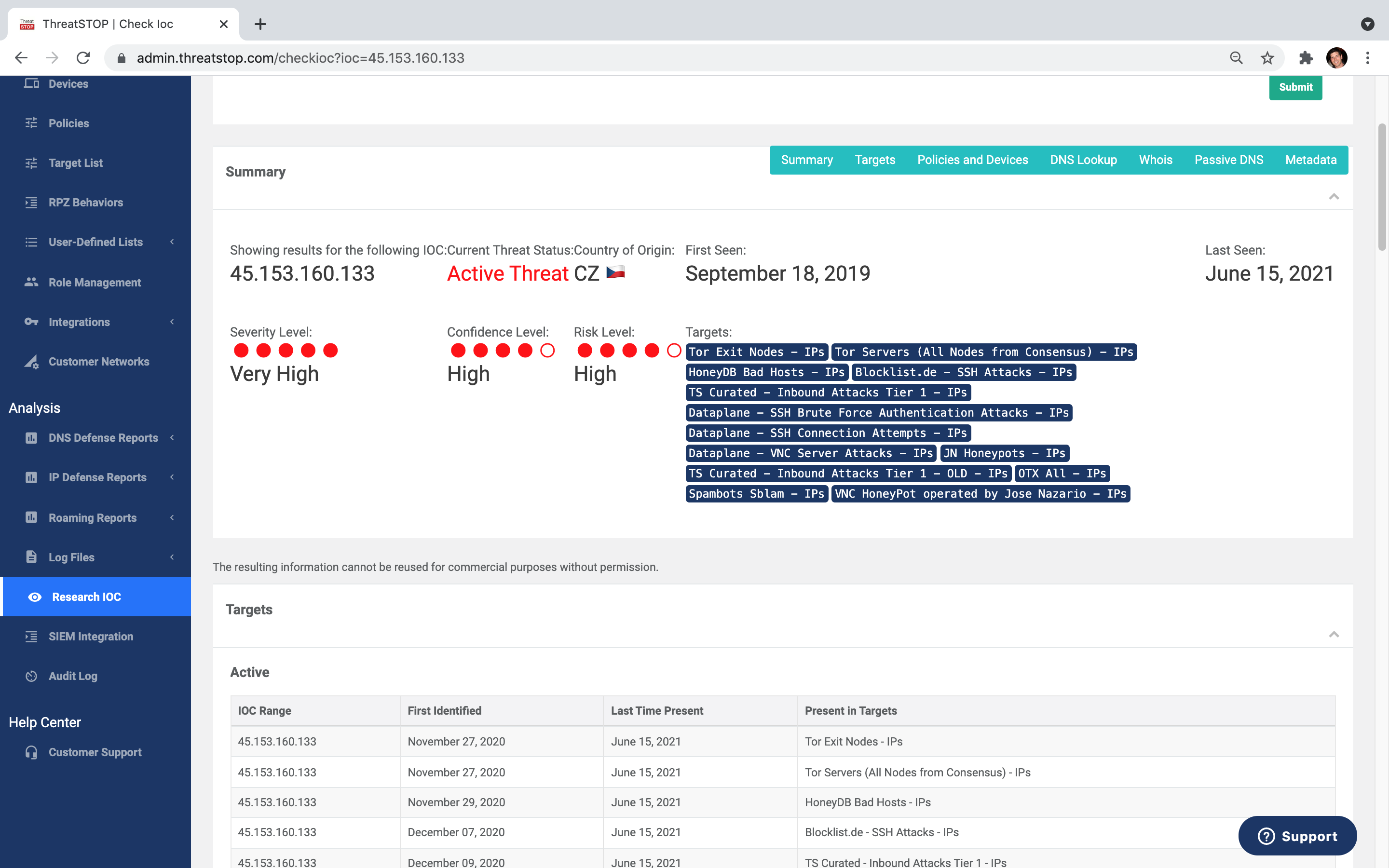
Comprehensive Threat Intelligence
Over 900+ qualified data sources that are human & machine curated, delivering the most comprehensive and accurate coverage in the industry of IP addresses and domains.
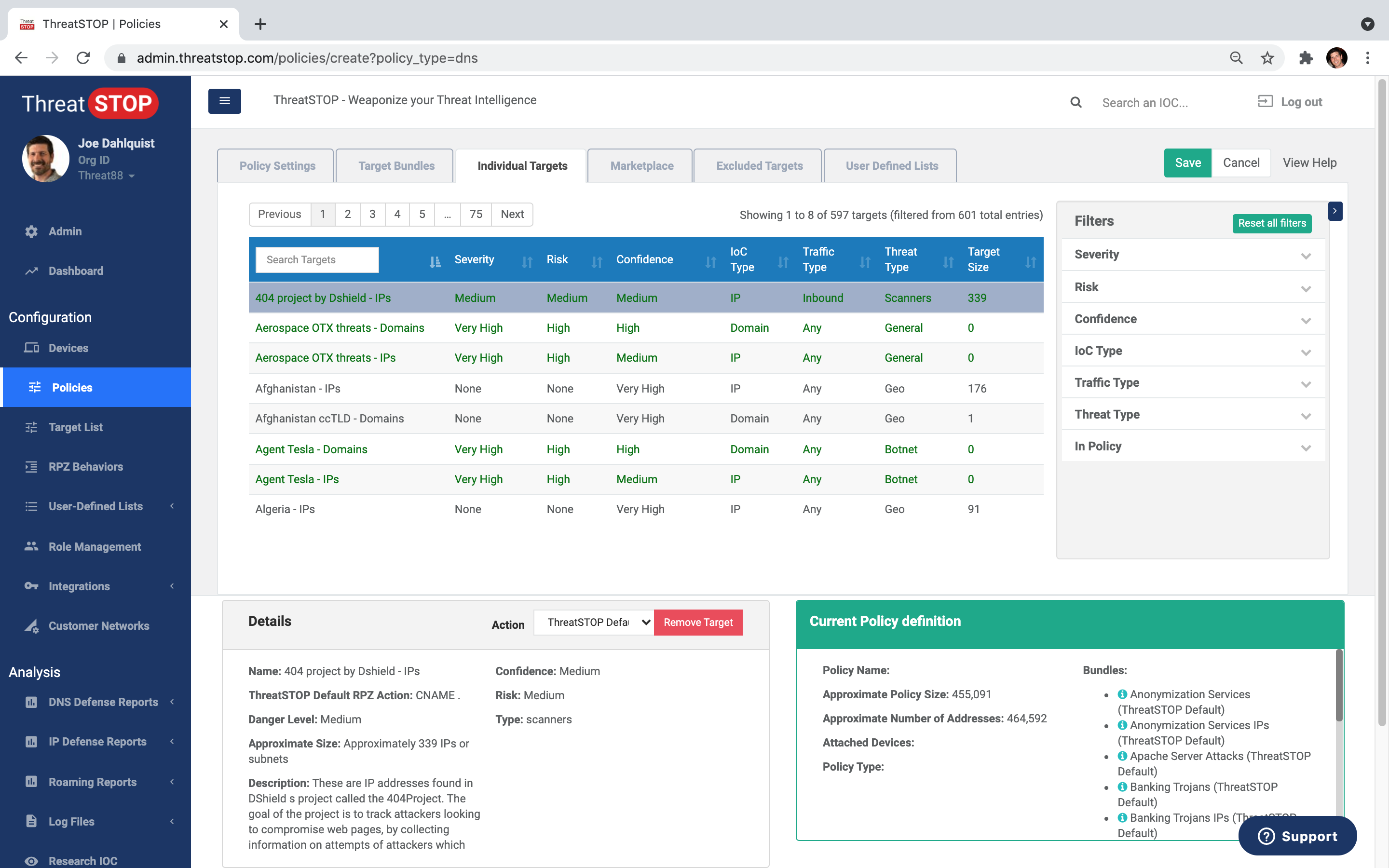
Custom Security Policies
Fine grained control with 600+ fully customizable policies in 60+ categories. Tailor your own custom block & allowlists.
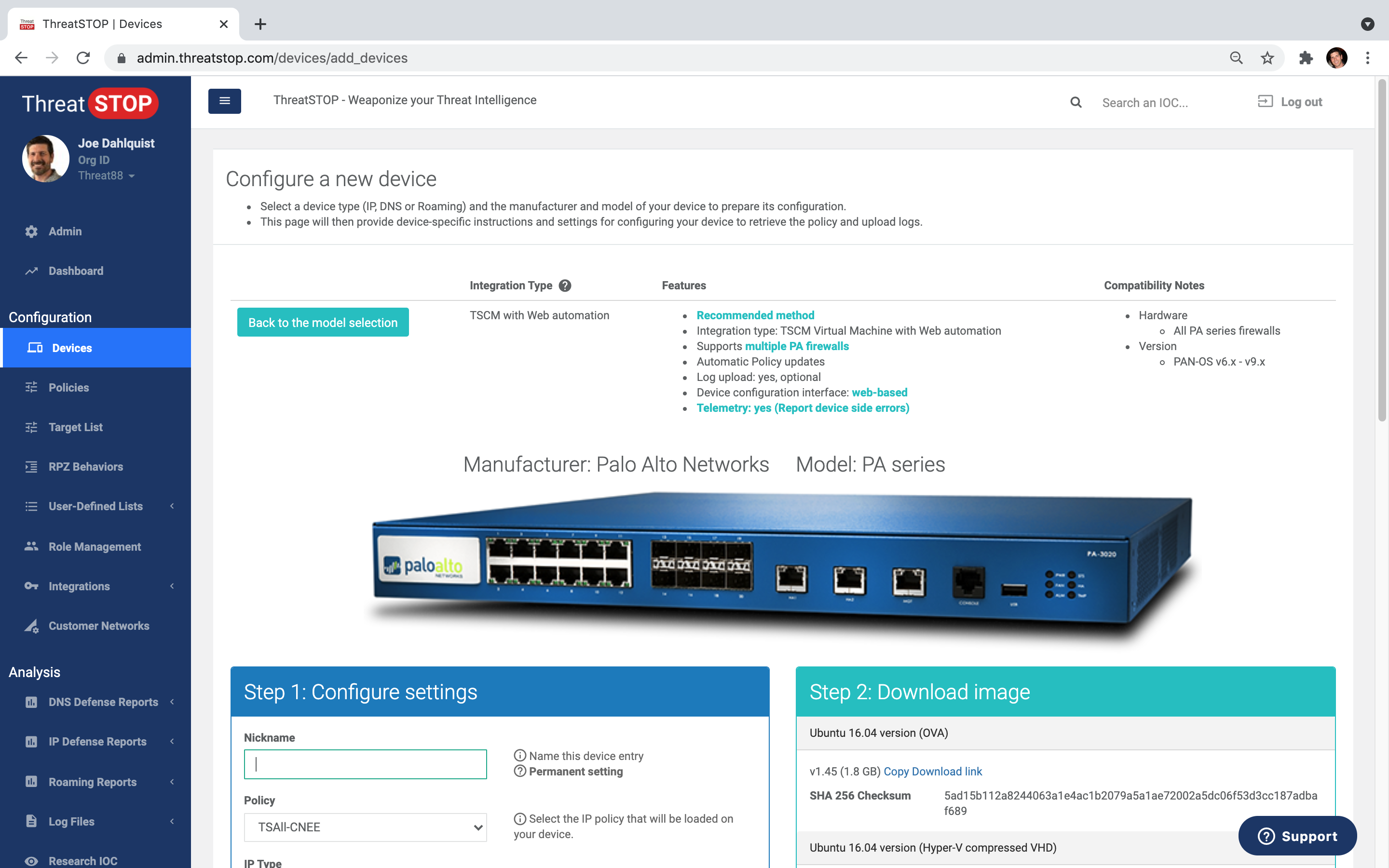
Network Device Integrations
Automated policy updates for virtually any NGFW, DNS server, Router, Switch, IDP, WAF, SIEM and more.
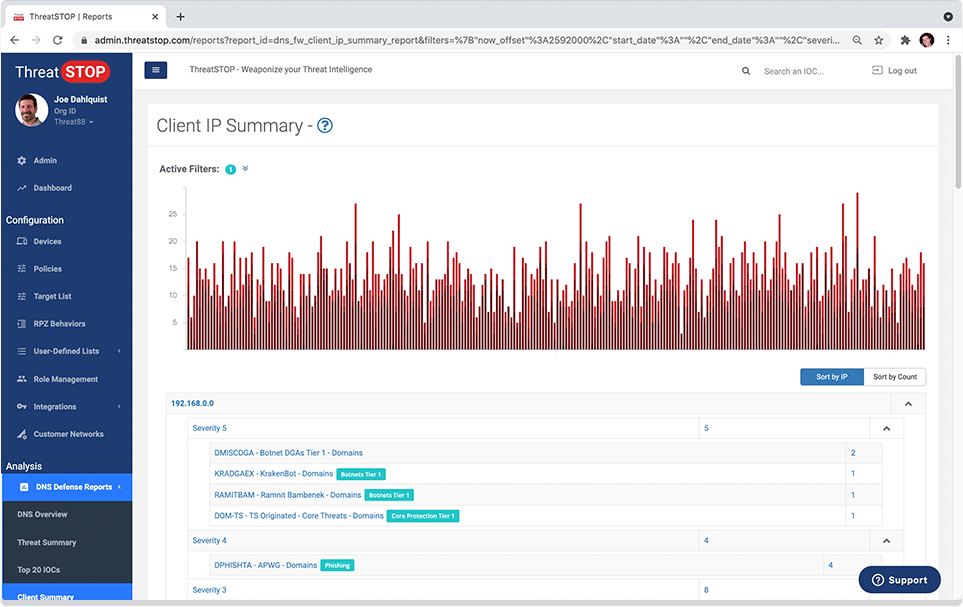
Forensics and Reporting
View & analyze blocked threats. Identify affected client devices. Custom email reports & alerts.
Free Trial

Solutions by industry

Education
Community colleges and universities are up against significant security challenges, including open environments and BYOD. Faculty, staff and students from all over the world converge on the same network storing sensitive data, all which must be protected to comply with HIPAA, FERPA and PCI.

Healthcare
Medical records are cyber's new goldmine. Not many industries can say that cybersecurity is a life-and-death issue, except for healthcare institutions. Equipment that we have come to rely on to diagnose critical illnesses and provide life support are now embedded with computers that can’t easily be modified.

Service Providers
Like every hosting company, Armor needs to protect their customers against botnets, phishing, zero-day and other advanced threats. They also need to provide the security that's required for customers with HIPAA, PCI and other compliance requirements.

Enterprise
Before becoming a ThreatSTOP customer, the global equipment manufacturer had every flashy security product implemented in their network - yet they were still constantly being attacked. With all systems showing zero gaps, and no unpatched areas, the manufacturer needed a solution that would prove effective in reality.

Public Agency
They had about 1,000 visitors (mostly students) use the library’s PCs and, with their laptops and mobile devices, their Wi-Fi network per day. These users were constantly getting infected, while the library was constantly blacklisted by the ISP and its Internet access blocked due to the large number of botted machines and active malware on the network.

SMBs
For a small company with one location and remote contractors coming in through VPN, Phoenix Energy was reasonably protected, and it had not experienced any major breaches in recent years. But Carol Maffitt, Phoenix Energy’s CIO, wanted an extra layer of protection, for added peace of mind.
Managed Service Providers
Grow your business and margin with the industry's most powerful DNS Filtering Solution.
Designed for multi-tenant use with easy-to-use enterprise features.